Checking NuGet package vulnerabilities with OWASP SafeNuGet
Edit - October 14, 2016 - We have a new, integrated vulnerability scan service.
A couple of days ago, OWASP released a new NuGet package which is able to check known vulnerabilities in NuGet packages. Use of libraries with known vulnerabilities can be an issue for software and components you create: check the excellent whitepaper "The Unfortunate Reality of Insecure Libraries". In the OWASP Top 10 2013, consuming vulnerable packages is listed under A9 Using Known Vulnerable Components.
There is a simple solution to this: by installing one additional package in your projects, automatic checking for known vulnerabilities can be done. The SafeNuGet package contains an MSBuild task which will warn you about this.
A repository with vulnerable packages and the reason for that can be found on the SafeNuGet GitHub project. When running a build which references vulnerable NuGet packages, the warnings list will contain some information about this as well as a link with some explanation:
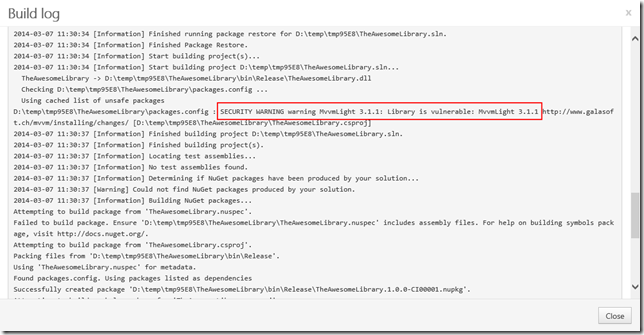
And of course when such library is built using MyGet Build Services, a warning will also be displayed in the build log:
It would be great if the build would fail entirely when such package is found, right? Well, that is a simple configuration parameter for the SafeNuGet package. Find the SafeNuGet.targets file and update its contents to:
<Project ToolsVersion="4.0" xmlns="http://schemas.microsoft.com/developer/msbuild/2003">
<UsingTask AssemblyFile="SafeNuGet.dll" TaskName="SafeNuGet.AreNuGetPackagesSafe" />
<Target Name="AfterBuild">
<AreNuGetPackagesSafe ProjectPath="$(MSBuildProjectDirectory)"
CacheTimeInMinutes="10" DontBreakBuild="false" />
</Target>
</Project>
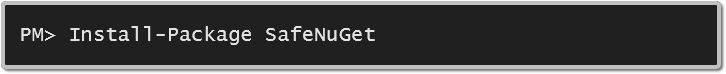
Want to make sure known vulnerabilities are shown in your builds? You know the drill:
Happy and safe packaging!